NGINX is the industry’s most ubiquitous API gateway, an infrastructure component that processes API traffic in API management solutions like those from Apigee, Axway, IBM DataPower, Kong, Red Hat 3scale, and Torry Harris. Combine that with the fact that more than 40% of the users we surveyed in 2018 have deployed NGINX Plus as an API gateway, it’s fair to say that NGINX is processing most of the world’s API traffic. That’s not too shabby, considering that Akamai puts API traffic at 83% of the world’s Internet traffic.
Why is NGINX so ubiquitous in the world of APIs? Because NGINX delivers high performance, security, and authentication services – all critical to your API environment. NGINX prevents DDoS attacks by enforcing rate limits on requests or bandwidth limits on specific users, and NGINX Plus provides authentication and fine‑grained access control to protect API‑based services.
The bottom line is that an API gateway is a critical component in overall API security. But you need to ask yourself: how secure is your API gateway itself? This blog explains why the security of the API gateway is important and how to think about the risk of exploiting it.
Bare Naked API Management Solutions
All the API management solutions listed above either use a customized version of NGINX Open Source or (as in the case of Kong) are built on third‑party modules such as OpenResty. OpenResty is an extensible and flexible platform based on NGINX and LuaJIT that is widely used by developers for customization and for certain use cases. Although OpenResty is fast, it’s not as fast as native NGINX with raw configuration files and no Lua modifications.
Further, solutions built using OpenResty can potentially leave you exposed to critical vulnerabilities. Consider a situation where the NGINX team discovers a critical vulnerability. Although rare, there have been five such vulnerabilities over the last three years. When such an issue is found in NGINX, all our customers using NGINX Plus receive a patch as soon as our engineering team fixes this issue. Our open source users receive this patch and the CVE notification usually within a week or two.
What about modified NGINX builds like OpenResty? Despite the best efforts of the OpenResty team, it is entirely reasonable to expect some delay as it takes time to qualify, port, and test bug fixes. Then this delay cascades through dependent products such as Kong which are even further from the base NGINX software.
As an example, for two CVEs about vulnerabilities in HTTP/2 discovered in fall 2018 (CVE-2018-16843 and CVE-2018-16844), we applied security patches to NGINX Plus R16 and NGINX Open Source 1.15.6. OpenResty issued a release candidate on March 3, 2019 that incorporated the fixes – a full fourth months after our patches. Solutions built on top of OpenResty such as Kong consequently take even longer to patch their codebase. In Kong’s case, they don’t even seem to share the same sense of urgency as OpenResty does in patching their core – the last CVE update incorporated by Kong was back in March 2018!
This leaves a substantial window of opportunity for bad actors to exploit these solutions, with your APIs, applications, and backend servers and processes all exposed. A key function of your API management solution – providing security – can be compromised.
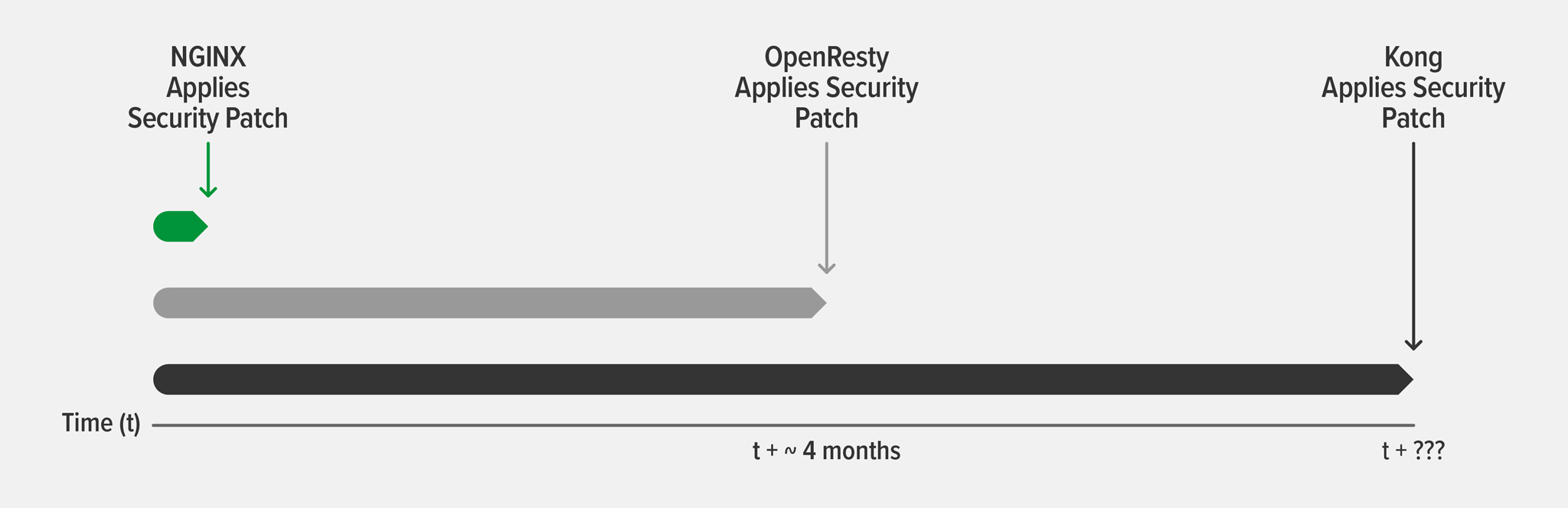
The figure illustrates typical timeframes we’ve observed for recent CVE patches to API management solutions built on top of NGINX Open Source. Security patches are immediately applied to NGINX Plus and NGINX Open Source. The timeframe for integrating NGINX patches is completely up to OpenResty and API management solutions such as Kong that use NGINX Open Source.
Peace of Mind with NGINX’s API Management Module
With the rise of the API economy, trust becomes central to your API ecosystem consisting of third‑party developers, suppliers, distributors, resellers, and even customers. Trust is an important concern for API architects, developers, I&O, and DevOps teams, and a core tenet of the NGINX Controller API Management Module. We provide you with the peace of mind and assurance that security issues discovered in NGINX Plus (the underlying gateway that handles API traffic in our API management solution) are addressed immediately.
[Editor – The NGINX Controller API Management Module is now API Connectivity Manager, part of F5 NGINX Management Suite.]
Do you know if your API management solution is built on NGINX? If so, do you know if your solution has incorporated all the latest security patches? We’d love to hear from you in the comments below. In the meantime, if you’re ready to go with a more trusted and secure solution, request a free 30-day trial of NGINX Controller [NGINX Management Suite].