Defense-in-depth refers to a security strategy composed of multiple, independent layers of security controls that continue to operate even if one layer fails or is compromised. It typically includes different types of security controls, such as people, technology, and operations. Layering these controls can help ensure attacks not mitigated at one point during data processing are blocked by another control layer in the same system.
There are many ways to achieve a defense-in-depth strategy. When it comes to technology components, we recommend starting with three items:
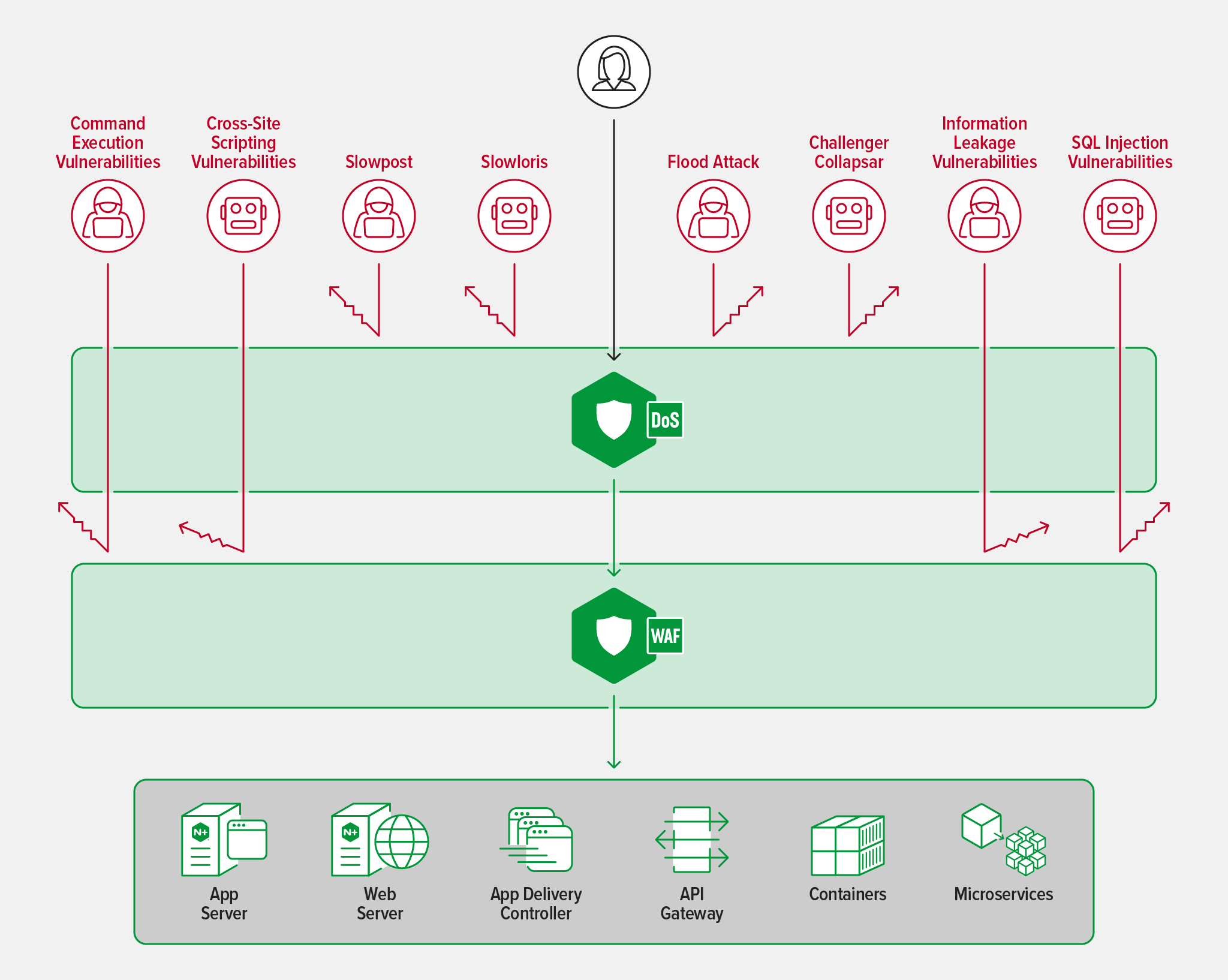
- Denial-of-service (DoS) protection – Deploy DoS protection to block DoS attacks so they can’t overwhelm your apps, ensuring a better and more predictable customer experience. DoS protection works best when deployed globally at the perimeter to ensure that all applications, APIs, and services – as well as other traffic management and security tools – are covered. For optimum effectiveness, the DoS solution also blocks distributed denial-of-service (DDoS) attacks, which leverage a large number of bots or compromised systems to direct a high volume of traffic at a specific web property, application, or one or more IP addresses.
- Web application firewall (WAF) – Deploy a WAF between the DoS protection layer and your load balancer or Ingress controller. A WAF protects against sophisticated Layer 7 attacks, such as the OWASP Top 10 vulnerabilities. The WAF must support custom configurations you define for specific use cases while also providing strong out-of-the-box default protections set up for developers who may not be as sophisticated in security practices.
- Authentication and authorization – Ensure your traffic management tools – such as load balancers, API gateways, and Ingress controllers – are properly configured to authenticate and authorize all requests for access to applications and infrastructure. This is especially important in Kubernetes and microservices-oriented environments where services are loosely coupled and communicate via APIs that may be externally accessible as well. Creating robust, continuous authentication processes, including certificate authorities and, when human-exposed, multi-factor authentication (MFA) reduces attack surface by ensuring that the validity of any connection is continuously challenged and verified.
How Can F5 NGINX Help?
You can deploy NGINX solutions at all three layers of your defense-in-depth implementation:
- For protection against DoS and Layer 7 attacks, deploy the F5 NGINX App Protect DoS and WAF modules. Built on F5’s market ‑leading security technologies and integrating natively with other NGINX tools, NGINX App Protect supports a modular approach for flexibility in deployment scenarios and optimal resource utilization:
- NGINX App Protect DoS – Behavioral DoS detection and mitigation with consistent and adaptive protection across clouds and architectures.
- NGINX App Protect WAF – A strong, lightweight WAF that protects against a wide range of Layer 7 attack, including the OWASP Top 10 and enables PCI DDS compliance.
- For centralized authentication and authorization on your load balancer, API gateway, or Ingress controller, deploy F5 NGINX Plus and F5 NGINX Ingress Controller:
- NGINX Plus – The all-in-one load balancer, reverse proxy, content cache, and API gateway.
- NGINX Ingress Controller – NGINX Plus-based Ingress controller for Kubernetes that handles advanced traffic control and shaping, monitoring and visibility, authentication and SSO, and acts as an API gateway.